Sensitive data Classification for HIPAA,PCI DSS, GDPR, ISO 27001 ,CCPA and More
Discover the need for sensitive data classification to comply with major cyber compliance requirements like PCI DSS, HIPAA, GDPR, CCPA, ISO 27001, NIST 800-53, SOC 2.
Data classification is key to meeting and demonstrating compliance across various regulations like PCI DSS, HIPAA, SOX, and GDPR. These standards, each with unique goals and demands, require the precise identification and labeling of regulated data—such as health records, cardholder data, and financial documents—to ensure its proper protection. This guide provides practical strategies for data classification tailored to the specific regulations and standards relevant to your organization.
Sensitive data classification is a critical process that involves categorizing data based on its level of sensitivity and the impact that its unauthorized disclosure could have on an organization or individuals. This foundational step in data protection helps businesses and organizations comply with various regulatory standards such as PCI DSS (Payment Card Industry Data Security Standard), HIPAA (Health Insurance Portability and Accountability Act), GDPR (General Data Protection Regulation), NIST (National Institute of Standards and Technology) frameworks, and ISO 27001.
By identifying the types of data that are considered sensitive, such as personal identification information, financial records, health information, and confidential business information, organizations can implement appropriate security controls and compliance measures.
This process not only safeguards the data from breaches and unauthorized access but also ensures that the organization meets legal and ethical obligations, thereby maintaining trust with clients, customers, and partners.
Through sensitive data classification, organizations can effectively manage risks, prioritize security efforts, and align their data protection strategies with industry standards and regulations.

Many organizations find the constantly changing and complex compliance requirements difficult to navigate. Compliance officers often struggle with the rapid pace and sheer volume of regulatory updates as a primary challenge. Additionally, a significant skills gap exacerbates the issue, with 60% of cybersecurity experts citing a global shortage of cybersecurity talent as a risk to their organizations.
Despite the widespread acknowledgment of data privacy as crucial to business, only 33% of security professionals prioritize data protection and governance as key responsibilities in their roles.
Various laws and standards, specific to different industries and regions, mandate compliance regulations for data classification.
The primary objective of these regulatory frameworks is to guarantee that organizations manage data with the utmost regard for privacy, security, and ethical considerations. Adherence to these regulations is essential for organizations to safeguard sensitive information, thereby preventing data breaches, avoiding legal consequences, and circumventing substantial financial penalties.
Moreover, compliance fosters trust among customers and stakeholders, as it showcases an organization's dedication to upholding data privacy and ensuring the security of personal and sensitive information. This commitment to compliance not only protects the organization but also reinforces its reputation as a trustworthy and responsible entity in managing data.
Healthcare organizations handle massive volumes of sensitive data daily; from patient identifiers to diagnostic histories; and classifying this information is essential for protecting both patients and the institution’s reputation. Sensitive data classification ensures that protected health information (PHI) and personally identifiable information (PII) are labeled according to risk levels, enabling organizations to apply the right security controls and meet compliance mandates such as HIPAA, GDPR, ISO 27001, PCI DSS, and CCPA.
Proper classification reduces the risk of breaches and unauthorized access while making compliance audits smoother and faster. With Strac, healthcare providers can automatically discover, classify, and remediate PHI/PII in real time across SaaS platforms, cloud storage, and collaboration tools—without deploying agents or slowing workflows. This unified visibility empowers healthcare teams to maintain confidentiality, integrity, and compliance seamlessly.
Healthcare data encompasses any information that relates to a patient’s physical or mental health, the provision of care, or payment for services. This includes patient demographics, medical records, billing data, lab results, and clinical notes; all of which often contain sensitive PHI.
Because this data flows across multiple systems (EHR platforms, SaaS tools, cloud drives, and even AI chat interfaces), identifying and classifying it becomes a cornerstone of risk management. Strac’s ML and OCR-powered data classification detects PHI across structured and unstructured data; including files, attachments, and chat messages; ensuring sensitive data is properly labeled and protected at every touchpoint.
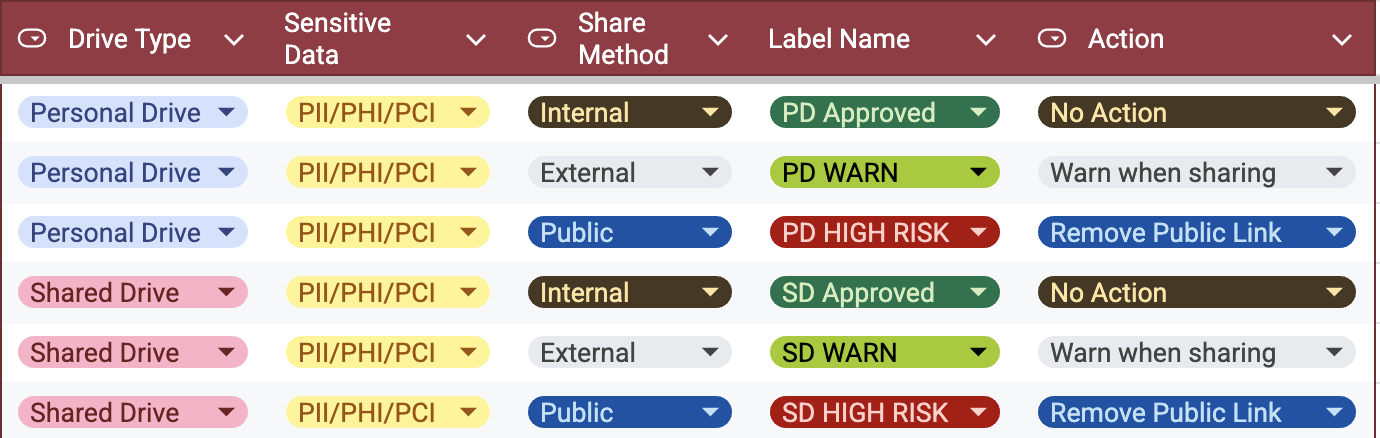
Healthcare organizations must categorize data based on sensitivity and usage to prevent mishandling or exposure. Key types of healthcare data that require classification include:
By classifying these datasets, healthcare organizations can assign the right access controls and apply policy-based protection. Strac automates this process; detecting and classifying PHI/PII across Google Drive, Slack, Salesforce, and other healthcare SaaS tools; to reduce manual oversight and accelerate compliance alignment.
Healthcare data classification is not just a compliance requirement; it’s a strategic defense mechanism. Without it, organizations risk:
Strac mitigates these risks by combining DSPM (Data Security Posture Management) and DLP (Data Loss Prevention) in one platform. It not only detects sensitive data but also applies real-time redaction, masking, or blocking to prevent leakage across SaaS apps, emails, and cloud systems; helping healthcare organizations protect data where it lives and moves.
Multiple global and regional frameworks govern how healthcare data must be classified and protected. Each sets its own requirements for data discovery, labeling, access, and protection controls:
Strac provides compliance-ready templates for each framework, automatically mapping classification policies to HIPAA, PCI, ISO 27001, and GDPR standards. Through agentless deployment, Strac helps healthcare institutions meet compliance faster; detecting, classifying, and remediating sensitive data across all digital environments in minutes.
Protect cardholder data (CHD) and ensure secure payment transactions.
Payment card information encompasses the credit card number (also known as the primary account number or PAN) when it is combined with any of the following elements:
A Netwrix 2020 Data Risk and Security Report found that 75% of financial institutions that classify data detect misuse within minutes—versus days or even months for those that don’t.

Data inventory and classification play a pivotal role in ensuring compliance with the European Union’s General Data Protection Regulation (GDPR). Although the GDPR text does not explicitly mention "data inventory" or "mapping," these processes are indispensable for safeguarding personal data and establishing a data security program aligned with data privacy laws.
For instance, conducting a data inventory is a fundamental step towards fulfilling the GDPR's mandate to keep records of processing activities. This involves identifying the categories of data, the purposes for which it is processed, and providing a general outline of the technical and organizational security measures in place.
Organizations are required to conduct a Data Protection Impact Assessment (DPIA) that encompasses all activities related to the collection, storage, utilization, or deletion of personal data. The DPIA should evaluate the significance or confidentiality of the data and the potential impact on privacy rights or distress that individuals might experience in the event of a security breach.
The GDPR protects personal data defined as any information that can be used to identify a natural person, either directly or indirectly. This includes, but is not limited to:
Effective GDPR data classification necessitates organizations to take into account various aspects of the data, such as:
The record-keeping obligations under GDPR have substantial similarities with those outlined for ISO 27001 compliance. Therefore, adopting the ISO 27001 framework not only facilitates GDPR compliance but also ensures a robust approach to data management and security. By leveraging the structured processes and detailed record-keeping practices of ISO 27001, organizations can efficiently meet the GDPR requirements, thereby enhancing their data protection efforts and compliance posture.
ISO/IEC 27001 is a globally recognized standard for creating, implementing, maintaining, and continually improving an Information Security Management System (ISMS). This standard, applicable to organizations of all types and sizes, aims to ensure the protection of information assets. When undergoing an ISO 27001 audit, organizations are expected to demonstrate a thorough understanding of their information assets, including their value, ownership, and the ways in which the data is used internally.
Unlike specific regulations that list exactly what data must be protected, ISO/IEC 27001 requires organizations to define the scope of their data environment themselves. This scope should take into account internal and external threats, the requirements of interested parties, and the interdependencies among the organization's operations. Therefore, it is the organization's responsibility to review all data within the defined scope to ensure comprehensive protection.
Data classification is a fundamental aspect of ISO 27001 compliance. The standard mandates that organizations conduct an inventory of information assets and classify this information to ensure it receives an appropriate level of protection. Although ISO 27001 does not prescribe a specific policy for data classification under ISO 27011, it does provide guidance in section A.8.2 on how to approach this task:
The flexibility of ISO 27001 allows organizations to tailor their data classification and protection strategies to their specific needs and risks, ensuring that information assets are appropriately secured against potential threats.
The National Institute of Standards and Technology (NIST) offers guidelines through Special Publication (SP) 800-53 for enhancing data security. This publication outlines security and privacy controls for federal information systems and organizations. It provides comprehensive advice on maintaining systems, applications, and integrations to safeguard the confidentiality, integrity, and availability of data.
NIST 800-53 is a mandatory framework for all federal agencies and their contractors but also serves as a valuable resource for private sector organizations.
NIST 800-53's approach to data classification categorizes information into three impact levels: low, moderate, and high. These levels are determined by the potential harm to agency operations, assets, or individuals that could result from a breach by either internal or external threats.
Each category—confidentiality, integrity, and availability—receives an impact value. The overall security impact level is then determined using the "high watermark" principle, meaning the highest impact level across confidentiality, integrity, and availability defines the final classification. Therefore, if any of the three criteria is assessed as high impact, the data's classification level is deemed high.
NIST 800-53 does not prescribe explicit classification levels for data as some standards do. However, NIST Special Publication 800-53 Rev. 5 includes categories such as:
Additionally, NIST allows for the definition of other categories by organizations. For example, data related to "Planning and Budgeting" may include budget formulation and capital planning, which generally have a low impact on confidentiality, integrity, and availability.
Yet, NIST advises organizations to consider special circumstances that could influence impact levels, like the early public release of budget drafts. This flexibility ensures organizations can tailor their classification to meet specific security requirements, aligning with NIST 800-53's overarching goal of protecting federal information systems while also offering guidance useful beyond government agencies.
The Health Insurance Portability and Accountability Act (HIPAA) Security Rule sets forth the administrative, physical, and technical safeguards required to protect the confidentiality, integrity, and availability of Protected Health Information (PHI).
Electronic PHI (ePHI), which includes any PHI that is stored on or transmitted by electronic media, falls under this regulation. Electronic storage media encompasses computer hard drives and removable media such as optical disks and memory cards, while transmission media includes the internet or private networks.
PHI data classification encompasses a wide range of patient details, including but not limited to:
HIPAA mandates that organizations ensure the integrity of ePHI, protecting it against unauthorized alteration or destruction. Covered entities and business associates must inventory their ePHI to identify risks to its confidentiality, availability, and integrity. This involves pinpointing where the ePHI is stored, received, maintained, or transmitted, which can be achieved through reviewing past projects, conducting interviews, and examining documentation.
HIPAA data classification guidelines advise organizing data based on its sensitivity level. This classification helps determine the baseline security controls necessary for data protection.
Organizations are recommended to adopt a three-tier data classification system:
By classifying data into these categories, organizations can more effectively apply the necessary security controls to protect ePHI, in compliance with HIPAA requirements, thereby ensuring the privacy and security of sensitive health information.
The Sarbanes-Oxley Act (SOX), while not explicitly mandating data classification, underscores the importance of implementing stringent data classification practices as a means to achieve compliance. Classifying and securing sensitive financial data enables companies to strengthen internal controls, deter unauthorized access, and maintain the accuracy and integrity of financial information. These measures are central to meeting SOX compliance requirements.
Effective data classification under SOX can facilitate compliance with several key sections of the Act:
By categorizing financial data according to its sensitivity and significance, companies not only enhance their compliance with SOX but also bolster their overall financial data security framework. This systematic approach to data classification aids in pinpointing which data is critical for accurate financial reporting and requires stringent protective measures, ultimately supporting SOX's objectives of promoting transparency, accountability, and trust in the corporate and financial sectors.
SOC 2 (Service Organization Control 2) is a framework for managing data based on five trust service principles: security, availability, processing integrity, confidentiality, and privacy. While SOC 2 itself does not specifically mandate data classification, effectively implementing its principles necessitates a robust data classification system. By identifying and categorizing data according to its sensitivity and relevance to these principles, organizations can establish the necessary controls to ensure compliance with SOC 2 requirements.
Although SOC 2 does not lay out explicit guidelines for data classification, it implicitly requires organizations to undertake comprehensive measures to manage and protect data in line with the trust service principles.
Data classification under SOC 2 involves several key actions:
By systematically classifying data in alignment with the SOC 2 framework, organizations can more effectively apply the necessary controls to protect and manage data. This not only helps in achieving compliance with SOC 2 but also enhances the overall security and integrity of the organization's data management practices.
The California Consumer Protection Act (CCPA) stands as a comprehensive privacy legislation designed to empower consumers with greater control over their personal information held by businesses.
Although the CCPA does not specifically outline data classification protocols, it places a significant emphasis on the protection and categorization of consumer data. Effective data classification under the CCPA is crucial for compliance, allowing businesses to efficiently organize, manage, and protect the personal information they collect.
By systematically categorizing data based on sensitivity, businesses can enhance their ability to identify, monitor, and secure personal information in alignment with CCPA requirements.
The CCPA mandates that organizations adopt strategies for the classification and management of personal data to ensure the protection of consumer privacy. While not prescribing specific data classification methodologies, the CCPA requires companies to perform several critical actions:
- Identify and categorize personal information: Businesses must accurately identify and categorize the types of personal information they collect, process, or store. This encompasses a wide range of data, including:
- Implement security measures: To comply with the CCPA, organizations are tasked with deploying robust security measures to protect personal data. This may involve the use of encryption, access controls, and other security mechanisms to prevent unauthorized access to sensitive information.
- Uphold consumer rights: The CCPA endows consumers with several rights concerning their personal information. These rights include the ability to inquire about the data being collected, request the deletion of their data, and opt out of the sale of their information. Effective data classification facilitates the identification and management of data relevant to these rights, enabling organizations to fulfill consumer requests efficiently.
- Ensure transparency and accountability: Businesses are required to be transparent in their data practices and accountable for the manner in which consumer information is handled. Through data classification, organizations can document and demonstrate their data management processes and compliance efforts, supporting the CCPA's transparency and accountability objectives.
By adhering to these principles and implementing a thorough data classification system, businesses can navigate the requirements of the CCPA more effectively, ensuring that consumer data is managed with the highest standards of privacy and security.
Given the broad scope of these regulations—and the complexity of modern IT environments—manual classification is no longer feasible at scale. Strac automates scanning and remediation to ensure that sensitive data is continuously discovered, classified, and protected:

Healthcare data classification is the foundation of modern compliance, data security, and patient trust. By identifying and labeling PHI, PII, and financial records across every system, healthcare organizations can ensure that data protection aligns with regulations like HIPAA, GDPR, PCI DSS, ISO 27001, and CCPA. Yet, manual classification is slow, error-prone, and costly.
With Strac’s agentless, ML-powered data classification, healthcare organizations gain:
The bottom line? Healthcare data classification isn’t just a compliance checkbox; it’s a proactive shield for patient privacy, institutional trust, and operational resilience. With Strac, organizations can meet every regulatory standard while protecting what matters most: sensitive health data.
Healthcare data classification is the process of identifying, labeling, and organizing sensitive healthcare information such as PHI (Protected Health Information) and PII (Personally Identifiable Information) according to its sensitivity level and compliance requirements. This process allows healthcare organizations to apply the right controls and prevent unauthorized access, data breaches, and compliance violations.
With Strac’s data classification engine, organizations automatically discover and tag PHI/PII across SaaS tools, cloud platforms, and endpoints. By classifying data accurately and in real time, Strac enables healthcare providers to strengthen data protection, reduce human error, and streamline compliance with HIPAA, PCI DSS, GDPR, ISO 27001, and CCPA.
Healthcare organizations must adhere to several global and regional data protection frameworks, each with specific requirements for how sensitive information is identified and secured. The most critical include:
Strac supports all of these through predefined compliance templates and automated classification rules, making it easier for healthcare providers to maintain full regulatory alignment without manual effort.
Healthcare data classification is central to HIPAA compliance because it ensures PHI is identified, secured, and monitored at all times. HIPAA requires organizations to know exactly where PHI resides, who has access, and how it’s protected. Classification provides that visibility; mapping all PHI within emails, SaaS apps, cloud drives, and communication tools.
Strac automates HIPAA compliance by continuously scanning and classifying PHI, applying redaction or masking in real time, and maintaining logs for audits. This proactive approach minimizes risks of unauthorized disclosure, supports HIPAA’s Security and Privacy Rules, and keeps compliance processes simple and verifiable.
Healthcare data classification can be complex because sensitive data exists in many formats; structured EHR records, unstructured notes, chat messages, or uploaded files. The biggest challenges include:
Strac overcomes these challenges through ML/OCR-based content detection that identifies PHI and PII with precision; across emails, chat, APIs, and cloud environments; ensuring no sensitive data slips through.
Accuracy in healthcare data classification depends on using technology that can interpret context, not just patterns. Traditional regex-based systems often miss sensitive data or generate false positives. Modern AI-driven solutions like Strac use machine learning, NLP, and OCR to understand data in context; whether in text, PDFs, or scanned medical forms.
To further ensure accuracy, organizations should:
By combining automation with human oversight, Strac ensures healthcare data classification remains precise, adaptive, and fully compliant; helping organizations safeguard patient privacy while maintaining operational efficiency.
.avif)
.avif)
.avif)
.avif)
.avif)






.gif)

