Top 5 Data Exfiltration Detection Tools for SaaS, Cloud & AI Security In 2025
Discover how leading DSPM and DLP solutions detect, block, and remediate sensitive data leaks across modern cloud and AI environments.

Data exfiltration detection tools are cybersecurity solutions designed to detect and prevent unauthorized data transfers or theft from an organization's systems. These tools monitor, flag, and often respond to suspicious behavior indicative of data leakage or theft, particularly involving sensitive information such as personal data, financial records, or proprietary business documents.
These tools are becoming critical in today’s cloud-first, AI-enabled environment, where sensitive data resides across SaaS apps, cloud storage, emails, databases, and even LLMs like ChatGPT.

The primary risk these tools mitigate is data loss—either through malicious insiders, compromised credentials, or external attacks. But they also solve for deeper operational and reputational issues. Here are a few scenarios:
The fallout of not having detection in place includes compliance violations (Strac Compliance), customer trust erosion, IP theft, and potential fines.

With rising complexity in hybrid and multi-cloud environments, an ideal tool must do more than just monitor. It should actively prevent, remediate, and learn from incidents. Here are must-have features:
You can’t protect what you can’t see. The tool should:
The tool should:
Detection is only half the battle. An effective solution must include:

Here are five top-tier solutions organizations can consider to detect and prevent data exfiltration. While each brings unique strengths, Strac stands out for its modern architecture, breadth of integrations, and proactive approach to remediation:
Below is a breakdown of the top 5 tools
Strac is a modern DSPM and DLP platform that proactively detects and remediates data exfiltration risks. With advanced sensitive data discovery, AI integrations, and real-time remediation capabilities like redaction, blocking, and encryption, Strac provides full visibility and control across SaaS, cloud, and AI apps. It’s fast to deploy and built for compliance with PCI, HIPAA, SOC2, and more.

Darktrace leverages machine learning and self-learning AI to detect unusual patterns in network activity. It builds behavioral baselines for users and devices and flags potential exfiltration attempts automatically.
Compared to Strac: Darktrace excels at behavioral analytics but lacks Strac’s proactive remediation (like redaction, deletion, encryption) and deep integrations with AI tools and unstructured data sources.

Varonis focuses on file and user behavior analytics to provide deep insights into access patterns. It detects and alerts on deviations that may indicate insider threats or data theft.
Compared to Strac: While Varonis is strong in user behavior analytics within file systems, it lacks the AI app coverage, real-time remediation, and flexible policy-driven controls that Strac offers across SaaS and cloud platforms.

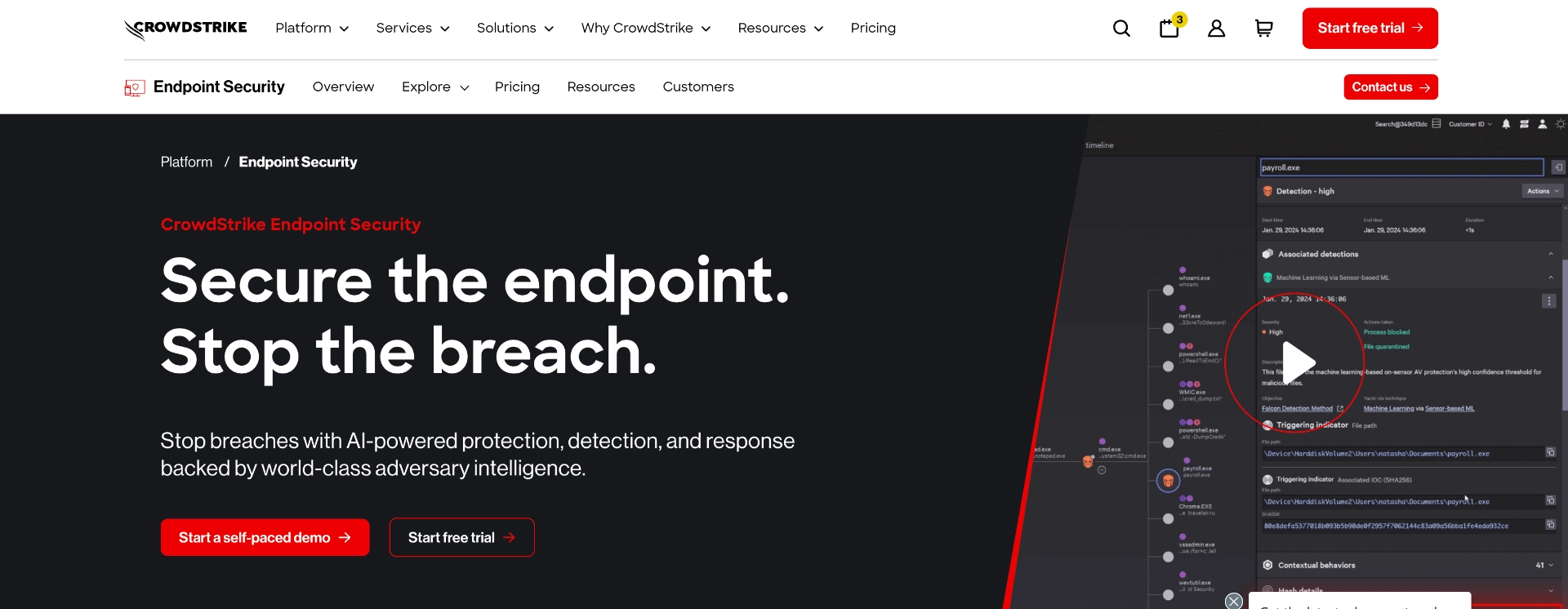
CrowdStrike Falcon is a comprehensive endpoint protection platform that includes real-time detection of suspicious data transfer activities. It’s known for advanced threat hunting and response capabilities.
Compared to Strac: CrowdStrike focuses heavily on endpoint protection and threat detection, but it doesn't offer the data discovery, SaaS/AI integration, or active remediation features that are core to Strac’s value proposition.
Proofpoint Insider Threat Management platform helps detect and prevent insider-driven data exfiltration, particularly via email, USB, and cloud apps. It offers detailed forensics and response tools.
Compared to Strac: Proofpoint offers strong insider threat monitoring, but it lacks Strac’s breadth in AI integration, real-time remediation capabilities, and ease of integration with a wide range of modern SaaS applications.

Strac is a powerful SaaS platform built for modern data environments. It’s a Data Discovery, DSPM, and DLP solution purpose-built to secure data wherever it lives—whether in your Salesforce instance, Slack channel, Google Drive folder, or OpenAI’s API calls.
Here’s how Strac addresses the data exfiltration challenge:
Check out what Strac customers are saying on G2 Reviews and see full integrations here.
Data exfiltration is no longer just a network security issue—it’s a data governance and compliance challenge. With the explosion of cloud apps and AI tools, sensitive data is more distributed and exposed than ever before.
Modern data exfiltration detection tools need to combine powerful visibility, advanced analytics, and proactive remediation to truly protect organizations.
Solutions like Strac bring all these capabilities together in a single, fast-to-integrate platform that works across your cloud, SaaS, and AI environment. Don’t wait for a breach to realize you need one.
Not always. Employees can unintentionally share confidential files with external parties, or upload sensitive data to AI tools without realizing the risks. Detection tools catch both intentional and accidental leaks.
Not exactly. While DLP prevents unauthorized sharing, detection tools monitor behavioral patterns and data movement. The best solutions (like Strac) combine both.
Even if data is exfiltrated, if it’s encrypted using strong, compliant standards, it becomes useless to the attacker.
AI apps. Employees paste sensitive content into ChatGPT or Copilot. Without AI-integrated detection tools, you’re flying blind.
Ideally, in milliseconds. Delays mean damage. Look for tools with real-time remediation like Strac.
.png)
.png)
.png)
.png)
.png)






.gif)

