Healthcare Data Classification: HIPAA Compliance & Security
Learn what healthcare data classification is, key types, HIPAA/HITECH links, best practices, trends, and how Strac automates healthcare data classification for PHI and PII.
Healthcare data classification is the backbone of modern healthcare security. A solid healthcare data classification system helps you find, label, and protect sensitive records across SaaS, cloud, EHR, and devices. Understanding healthcare data classification types is how you turn sprawling data into clear guardrails that satisfy HIPAA while raising your overall security posture.

Definition: Healthcare data classification is the structured process of discovering, labeling, and prioritizing healthcare data based on sensitivity and regulatory requirements. A healthcare data classification system assigns labels like Public, Internal, Confidential, Restricted (PHI/PII) that drive controls such as access, encryption, DLP, retention, and auditing.
Why it matters: In healthcare, PHI and PII appear in charts, claims, emails, chat, files, and even GenAI prompts. Precise labels make it easy to apply HIPAA controls, prevent accidental exposure, and enable quick, compliant incident response.
Examples: patient charts, diagnoses, lab results, imaging, prescriptions, care plans.
Why classify: Most clinical data is Restricted (PHI). Enforce least-privilege, encrypt at rest and in transit, and log every access.
Examples: billing, insurance, claims, eligibility, appointments, referral forms.
Why classify: Often Confidential (PII/financial). Apply DLP for account numbers, payer IDs, and anti-exfiltration for exports.
Examples: staffing schedules, facility logs, device telemetry, inventory, maintenance.
Why classify: Usually Internal but can include embedded PII. Classify to prevent aggregation risks and ensure vendor access control.
Practical tip: Start with these healthcare data classification types and map each to controls: label → encrypt → restrict → monitor → retain → dispose.

Understanding how healthcare data classification aligns with global regulations isn’t just about ticking boxes; it’s how hospitals, telehealth providers, and digital health platforms stay compliant and resilient. Below, we break down the four cornerstone frameworks shaping modern data protection in healthcare; and how classification makes each one actionable.
HIPAA remains the backbone of healthcare data security in the U.S., setting the standard for protecting Protected Health Information (PHI).
Data classification under HIPAA helps you:
Strac helps healthcare teams classify and redact PHI across apps in real time — enabling compliant access controls and continuous HIPAA alignment without manual overhead.
The HITECH Act expanded HIPAA by adding strict breach-notification requirements. Classification plays a crucial role in meeting them.
With Strac’s data discovery + classification engine, security teams can pinpoint breached PHI within minutes, not days — turning HITECH compliance into a measurable operational advantage.
For healthcare providers handling EU patients or operating internationally, GDPR defines PHI and PII as special-category data that requires explicit protection.
Classification under GDPR ensures you can:
Strac’s ML + OCR classification recognises patient identifiers even inside PDFs, imaging files, and chat logs — powering true GDPR compliance at scale.
For healthcare organisations or digital-health apps serving California residents, CCPA / CPRA add extra layers of control over Sensitive Personal Information (SPI).
Strac integrates these principles directly into its DLP policies — flagging, redacting, or blocking SPI before it leaves your environment.
Regulatory frameworks may differ in language, but they converge on one truth: you can’t protect what you don’t classify.
By embedding data classification into your DLP + DSPM strategy, you transform compliance from reactive paperwork into proactive governance — reducing breach costs, improving patient trust, and meeting every audit with confidence.
Also consider: HITRUST CSF, CMS Information Blocking Rule, state privacy laws, and payer requirements. A unified healthcare data classification system makes cross-framework alignment feasible.
HIPAA data classification is the foundation of healthcare data security. It is the process of organizing and labeling data based on its sensitivity, purpose, and regulatory requirements, ensuring that Protected Health Information (PHI) receives the highest level of protection.
In practice, that means separating a patient’s lab result from a marketing email or an insurance claim from internal notes, and applying the right controls to each. When PHI is not clearly classified, it can easily move into unsecured systems, triggering compliance violations, fines, and loss of patient trust.
HIPAA requires healthcare organizations to enforce administrative, physical, and technical safeguards to protect PHI. Data classification makes these safeguards actionable:
How Strac Helps:
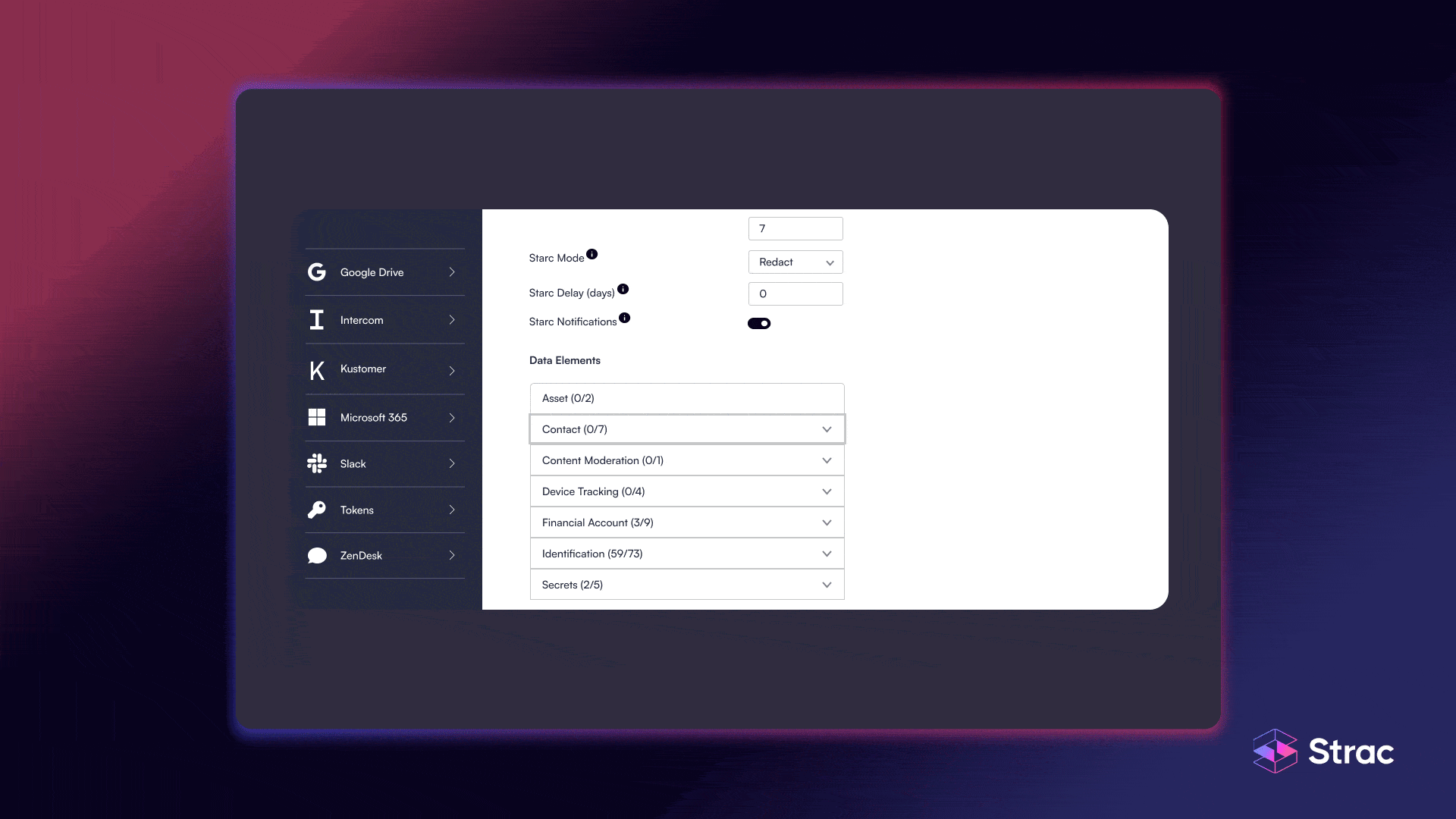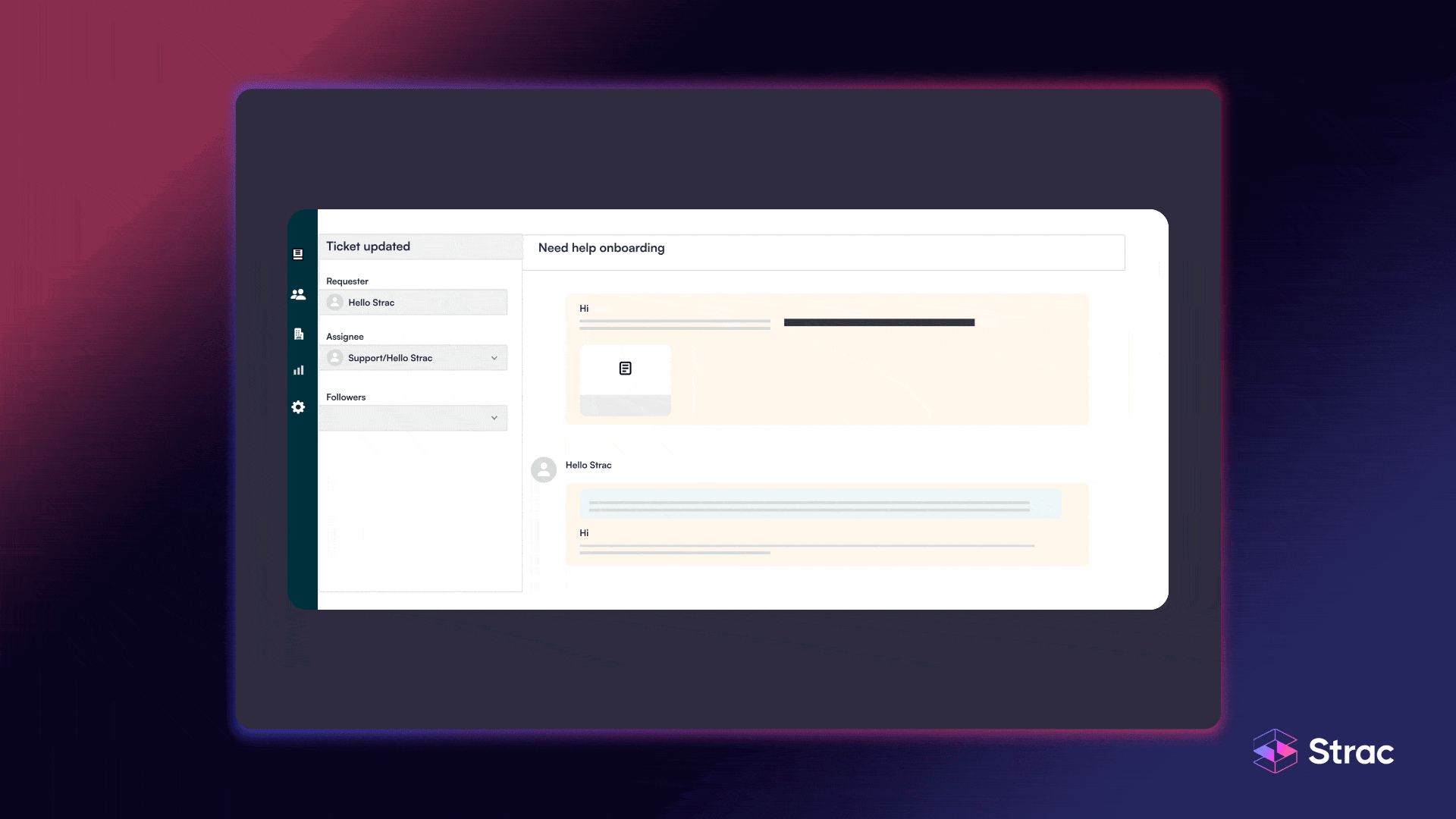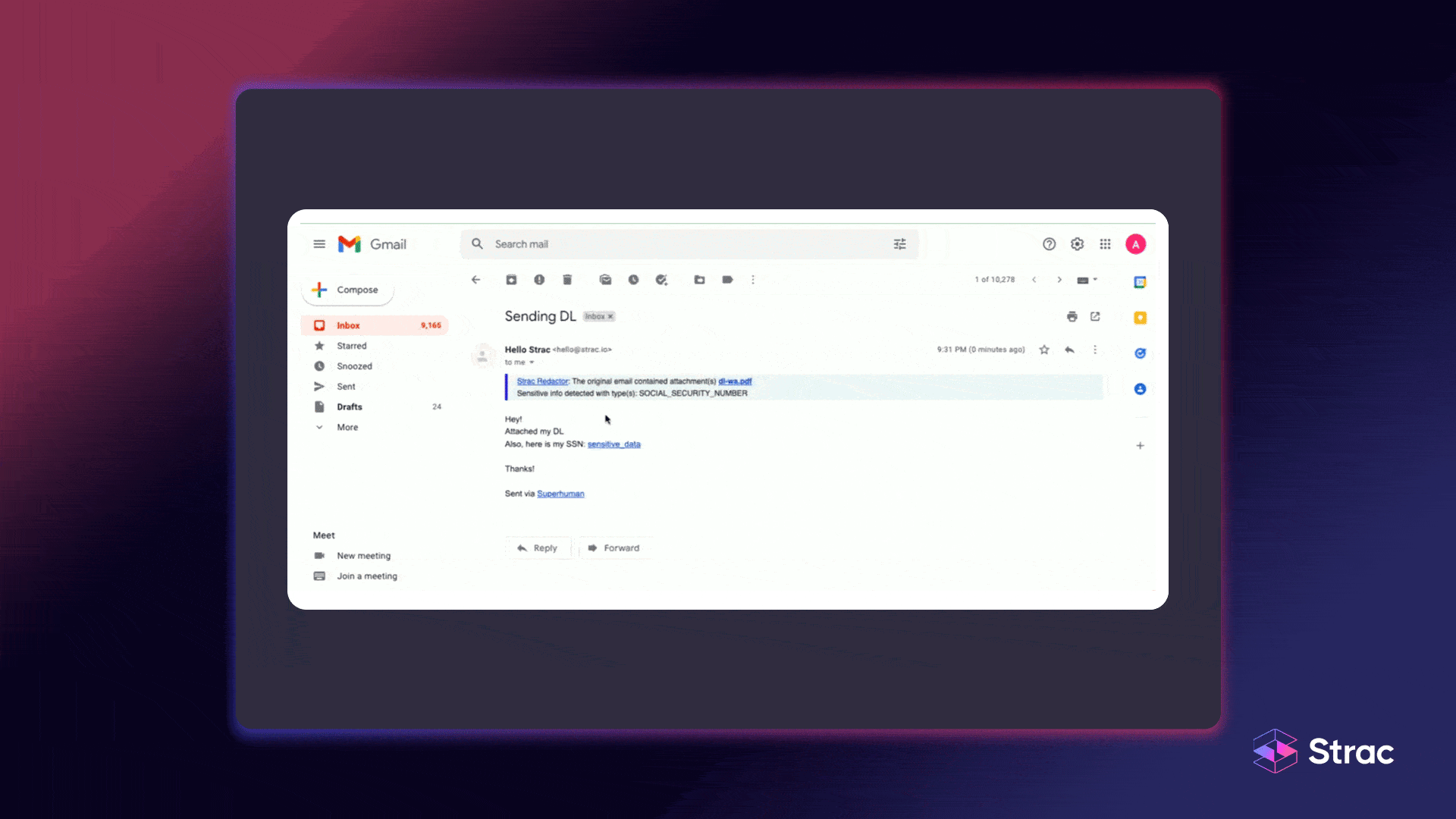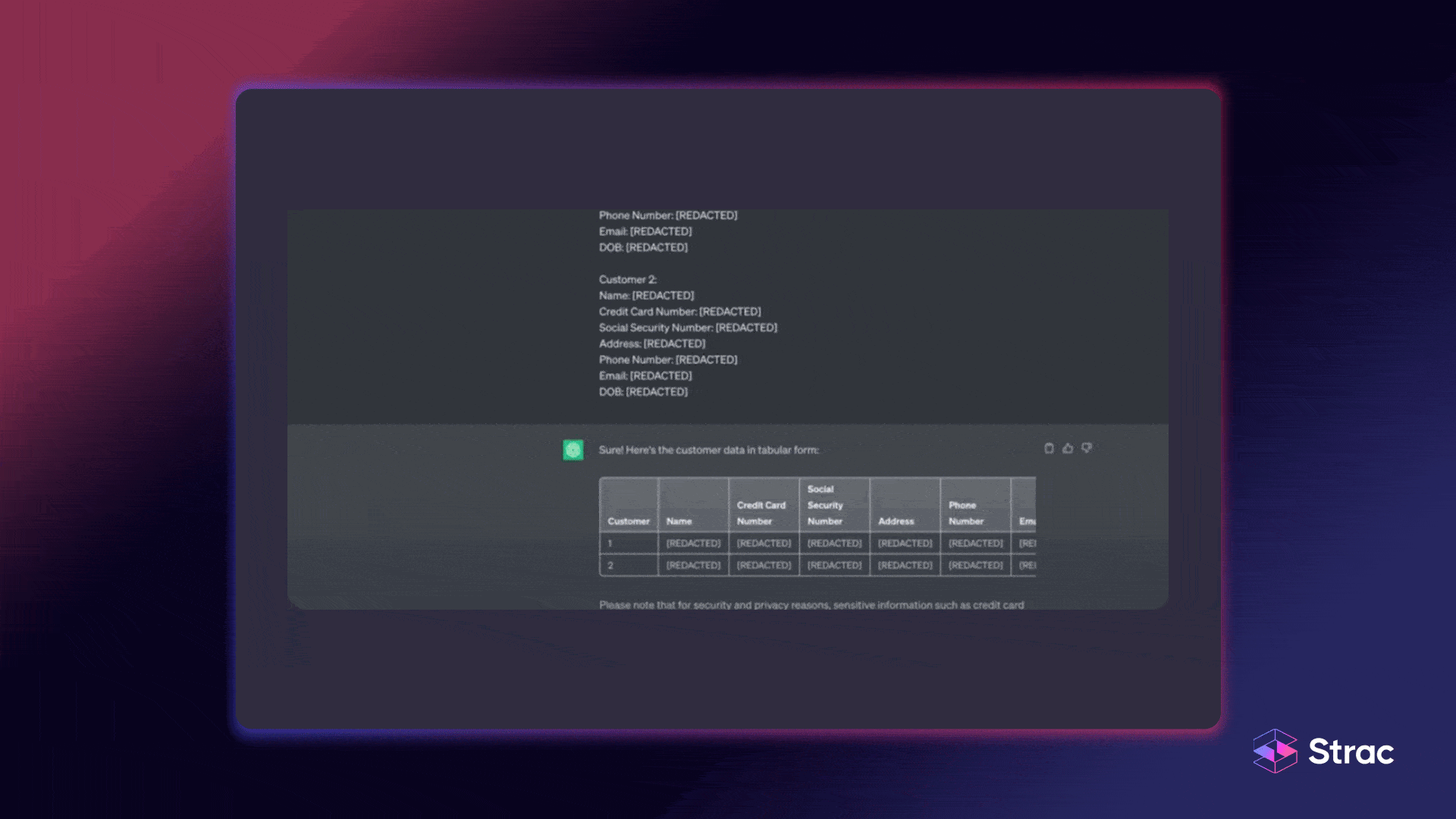
Strac automates HIPAA data classification across SaaS, cloud, and collaboration tools, identifying PHI in text, images, and files with machine learning and OCR precision. It does not just label data, it acts on it by instantly redacting, masking, or blocking PHI before it is exposed. With built-in HIPAA templates, audit logs, and inline remediation, Strac gives compliance teams confidence and control while keeping operations seamless.
In a world where clinical records, billing data, and patient communications move across SaaS apps, clouds, and AI tools in real time, healthcare data classification has become the backbone of compliance, security, and trust. For both providers and payers, it is no longer optional — it is how resilient healthcare systems are built.
Accurate classification ensures every piece of Protected Health Information (PHI) and Personally Identifiable Information (PII) is clearly labeled, guiding the enforcement of administrative, technical, and physical safeguards under HIPAA.
Automated labeling simplifies audits, maps data to specific HIPAA requirements, and dramatically reduces the risk of fines or non-compliance. Instead of relying on manual checks, compliance officers gain a real-time dashboard of where PHI lives and how it’s protected.
Classification powers the full data protection lifecycle — feeding DLP, tokenization, redaction, encryption, and quarantine workflows that prevent sensitive data from leaking through emails, chats, cloud drives, tickets, or GenAI tools.
When combined with Strac’s inline remediation, healthcare organizations can automatically block or mask PHI before it leaves the environment, stopping potential breaches before they happen.
A well-structured classification framework streamlines data routing, retention, and archival across departments. By reducing manual reviews, it frees up time for security and IT teams, accelerates incident response, and ensures that only the right people handle the right data.
For payers, automated classification also enhances claim processing speed and improves data-sharing accuracy between systems.
Patients are more likely to share sensitive information when they know their data is safe. Transparent, well-documented controls over PHI and PII demonstrate responsibility, strengthen brand reputation, and boost adoption of digital services such as patient portals and telehealth platforms.
Trust is not just earned through care — it is earned through secure, compliant, and transparent data practices.
Define labels, examples, required controls, retention periods, and escalation paths. Keep it short and unambiguous.
Adopt pattern + ML + OCR for scans, labs, faxes, and screenshots. Favor systems that detect PHI in SaaS, cloud, EHR exports, and GenAI.
Short, role-based sessions with real examples from your environment. Measure completion and understanding.
Map labels to groups and just-in-time access. Require MFA for Restricted data.
Quarterly label accuracy checks, policy drift reviews, and targeted red-team tests on PHI flows.
Centralize logs, detect anomalies, and alert on mass downloads, external shares, and unusual GenAI prompts containing PHI.
Use agentless discovery and incremental scans. Prioritize high-risk systems first.
Publish a single policy. Add tooltips and in-product helpers so labels are applied the same way in EHR, SaaS, and cloud.
Track updates and tie requirements to labels rather than to apps. Update once, propagate everywhere.
Choose APIs and native connectors. Bridge EHR exports to your DLP and DSPM layers for continuous coverage.
Context-aware models reduce false positives and recognize PHI inside images, scans, and screenshots.
Selective use for tamper-evident logs and consent receipts. Useful where audit integrity is paramount.
Your healthcare data classification system should learn from incidents, new data sources, and policy updates without re-architecting.
Strac combines DSPM + DLP to discover PHI/PII, apply labels, and enforce policies across SaaS, cloud, GenAI, browser, and endpoints. You get OCR-based detection for scans and screenshots, inline remediation like redaction, quarantine, tokenization, and access revocation, plus detailed audit for HIPAA, HITECH, GDPR, and CCPA.
A precise, automated healthcare data classification system is the simplest way to align with HIPAA, strengthen security, streamline operations, and build patient trust. Standardize labels, automate discovery, and enforce controls where work actually happens—SaaS, cloud, GenAI, and devices.
Next step: Book a short walkthrough to see Strac classify PHI and enforce policy across your stack. We will show discovery, labeling, redaction, and remediation in under 20 minutes.
Start with four: Public, Internal, Confidential, Restricted (PHI/PII). If you handle research or genomic data, add one more tier for Highly Restricted.
Anything that ties a patient to care: MRNs, DICOM with identifiers, discharge summaries, claims with names or addresses, and billing attachments with policy numbers.
Yes—pair labels with Browser DLP / GenAI DLP to detect PHI and block or redact before it leaves the device or browser. See Strac’s GenAI and browser controls.
Yes. DSPM finds and maps sensitive data; DLP enforces how it moves. Together they satisfy discovery, least-privilege, and transmission safeguards.
Onboard 3 sources in 30 days: email, cloud drive, and ticketing. Use auto-labels for PHI patterns, monitor first, then turn on redaction and quarantine.
.avif)
.avif)
.avif)
.avif)
.avif)






.gif)

